CyberFire Puzzles Fall 2021 Report
The Fall 2021 Cyber Fire Puzzles are complete! We want to say thank you and congratulations to everyone that participated, and we hope you had fun and learned some new tricks and tools along the way! Below is a brief writeup that details the total number of participants, the teams and their placements, the challenge categories offered, and the overall event results.
Introduction
The Fall 2021 Cyber Fire Puzzles ran from 11 AM CDT on Saturday, August 21, to 5 PM CDT the next day, August 22, giving a little over 24 hours for all the participants to solve challenges. There were **37 total applicants, with a mix of PhD, Master's, and undergradute students all participating. The event was offered both online and in person, with some teams competing in person, some teams competing online, and some teams having both in person and online participants, using the AUEHC Discord to communicate.
Teams
Teams were made up of groups of 2-6 students, with a total of 11 teams participating. The list of teams that participated in the even is below:
- admin
- APT28
- cpt-175
- CUPS
- DollarShort
- Alex Team Best
- book
- Lost
- Team name
- ZeroToNero
- Newbie
Categories
There was a large spread of different challenge categories offered, with everything from memory forensics to custom network protocol decoding. Some categories were the same as last year, but there were quite a few new categories this year. A list of the challenge categories for this year's puzzles are below:
- arena:
Analyze a disk image to find some suspicious activity.
- base:
Decode a custom base alphabet from base 2 to base 1337.
- codebreaking:
A variety of cryptography problems.
- linux_memory_intro:
Learn how to analyze Linux memory dumps.
- netarch-core:
Learn custom protocol and encryption routines.
- NetworkFundamentals:
Learn fundamentals of networking.
- PortsandProtocols:
Learn common networking ports and protocols.
- Safe_Malware:
Reverse engineer binaries to find a secret message.
- shadow:
Crack passwords to find the solution.
- steg:
Find the hidden message within a normal looking file.
Results
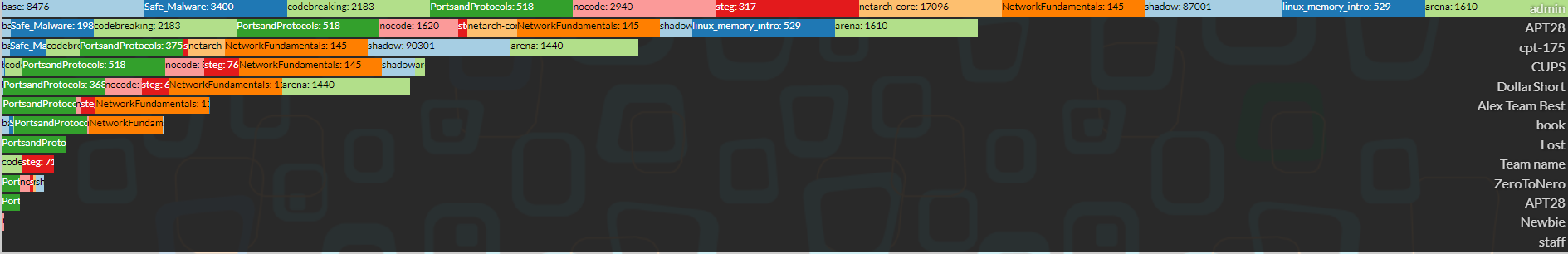
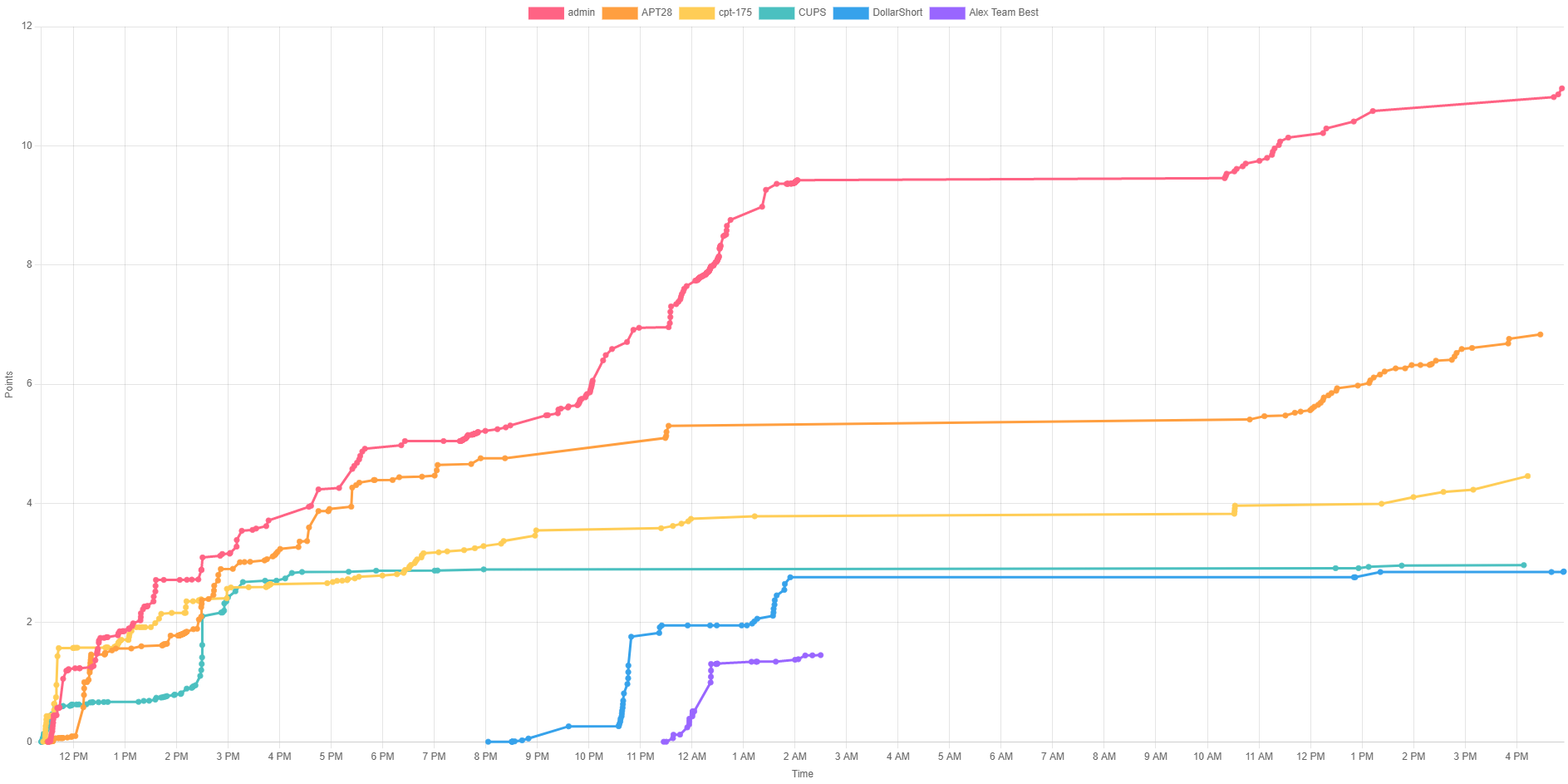
Congratulations to team admin (*ahem* cheaters) for coming in first place, team APT28 for coming in second, and team cpt-175 for coming in third, but congrats as well to every team that participated! Below are two pictures showing the teams' scores by time and their total points.

Team's Scores by Time
Breakdown of the Teams' Earned Points